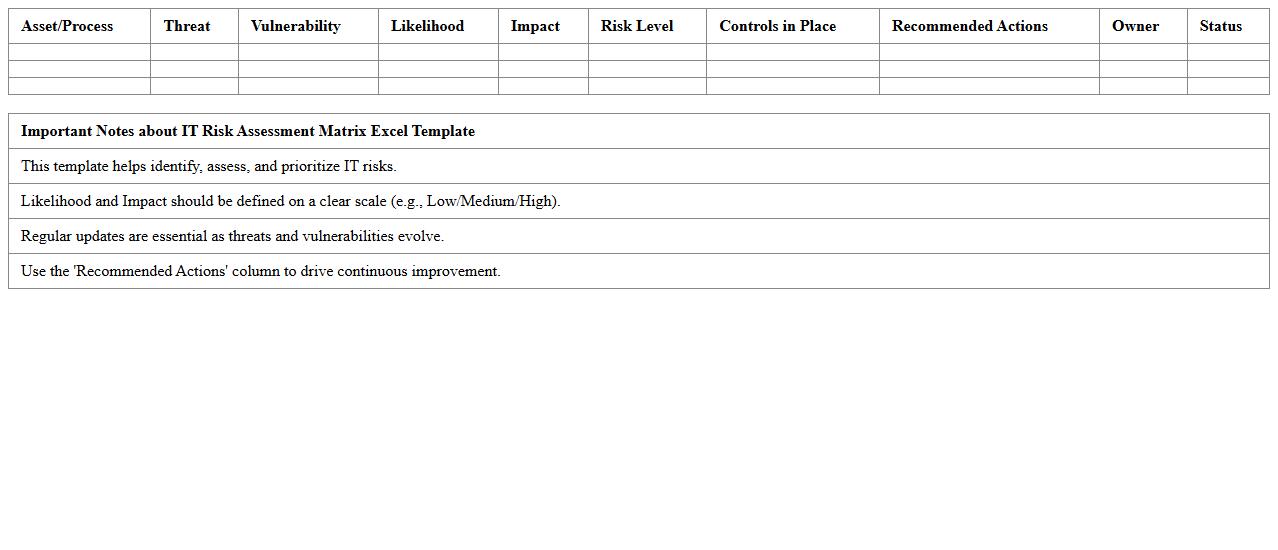
IT Risk Assessment Matrix Excel Template
The
IT Risk Assessment Matrix Excel Template is a structured tool designed to identify, evaluate, and prioritize potential IT risks by mapping their likelihood against impact levels. It helps organizations systematically visualize risk exposure, enabling data-driven decision-making for risk mitigation strategies. Using this template enhances risk management efficiency, supports compliance requirements, and improves overall cybersecurity posture.
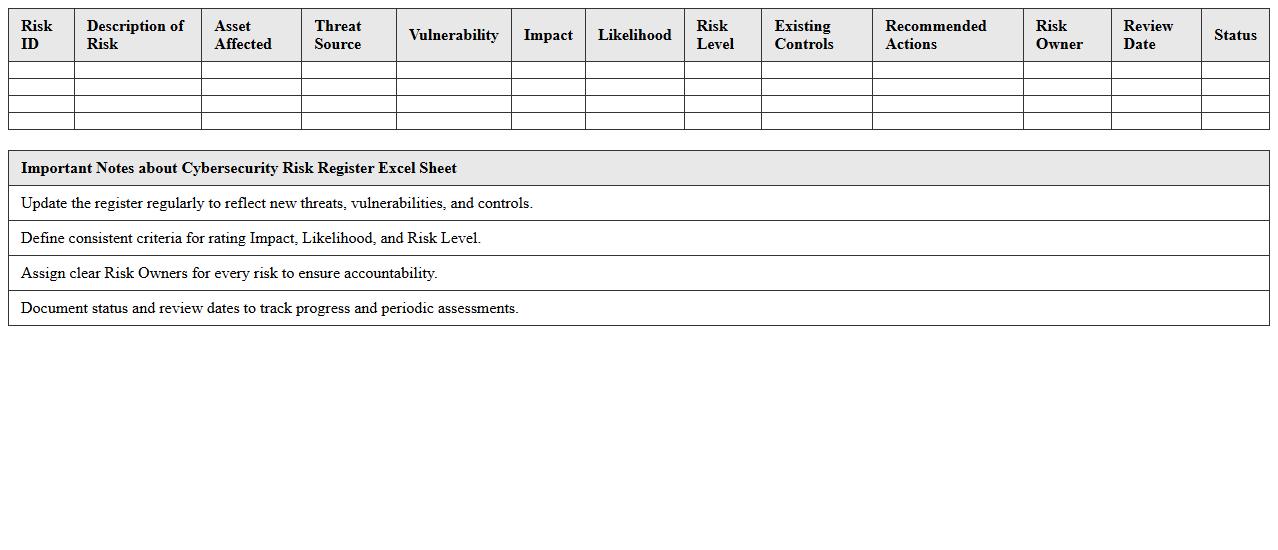
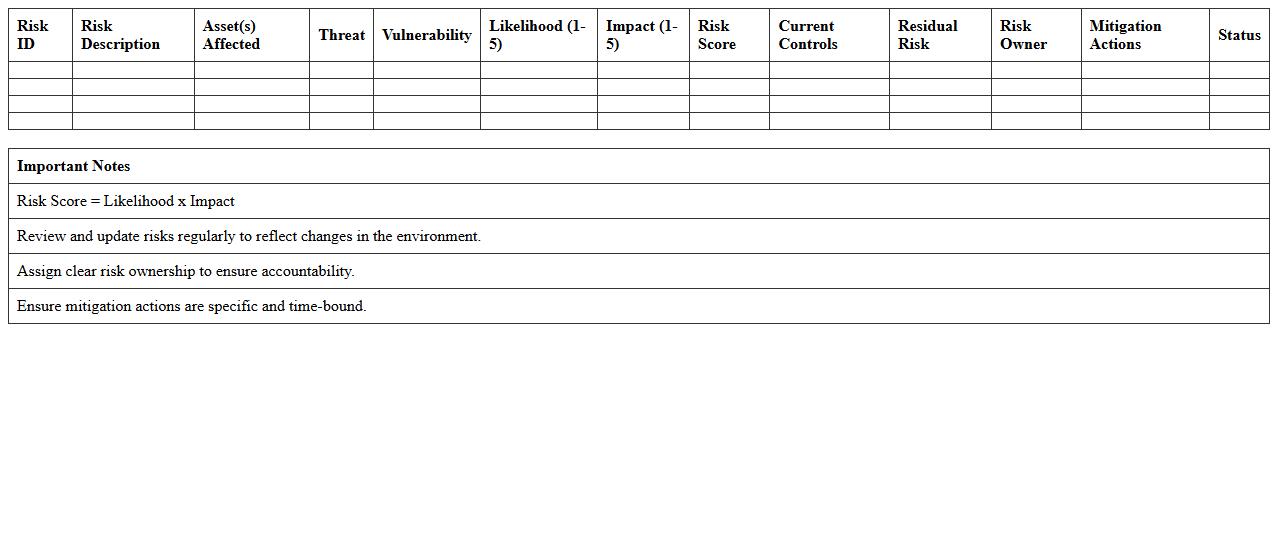
Cybersecurity Risk Register Excel Sheet
A
Cybersecurity Risk Register Excel Sheet is a structured document used to identify, assess, and manage cybersecurity risks within an organization. It helps track vulnerabilities, potential threats, risk levels, and mitigation strategies in a clear, organized format. This tool supports proactive risk management by enabling teams to prioritize security efforts and monitor progress effectively.
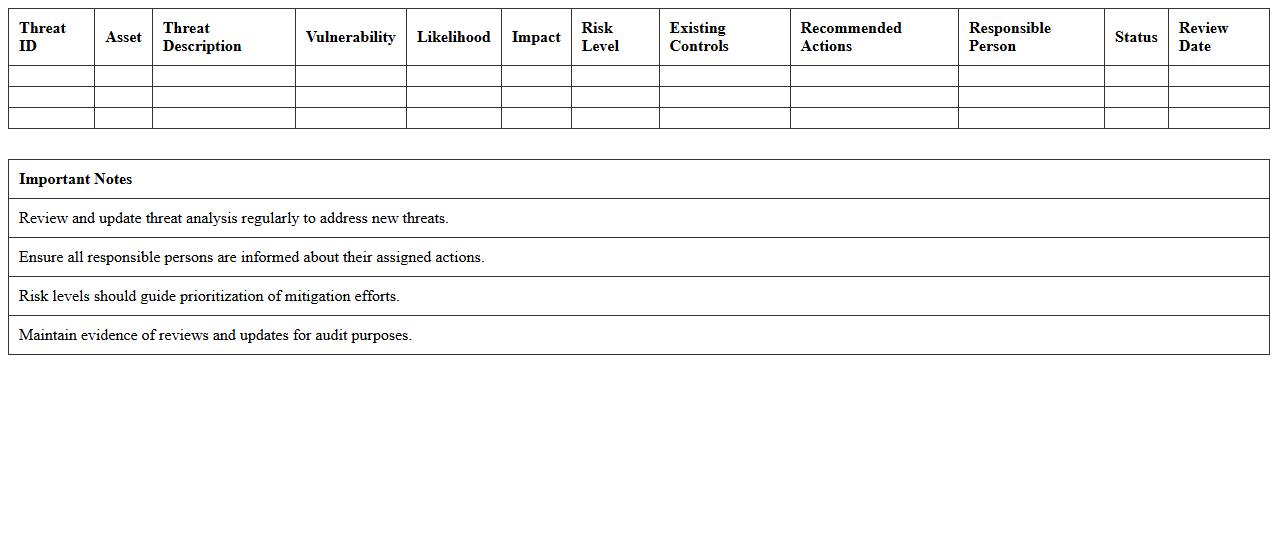
Information Security Threat Analysis Template
An
Information Security Threat Analysis Template document systematically identifies, assesses, and prioritizes potential security threats to an organization's information systems. It provides a structured framework for documenting threat sources, vulnerabilities, impact, and mitigation strategies, enabling organizations to proactively manage risks and strengthen their cybersecurity posture. Utilizing this template helps streamline threat evaluation processes, ensure comprehensive risk coverage, and support compliance with security standards and regulatory requirements.
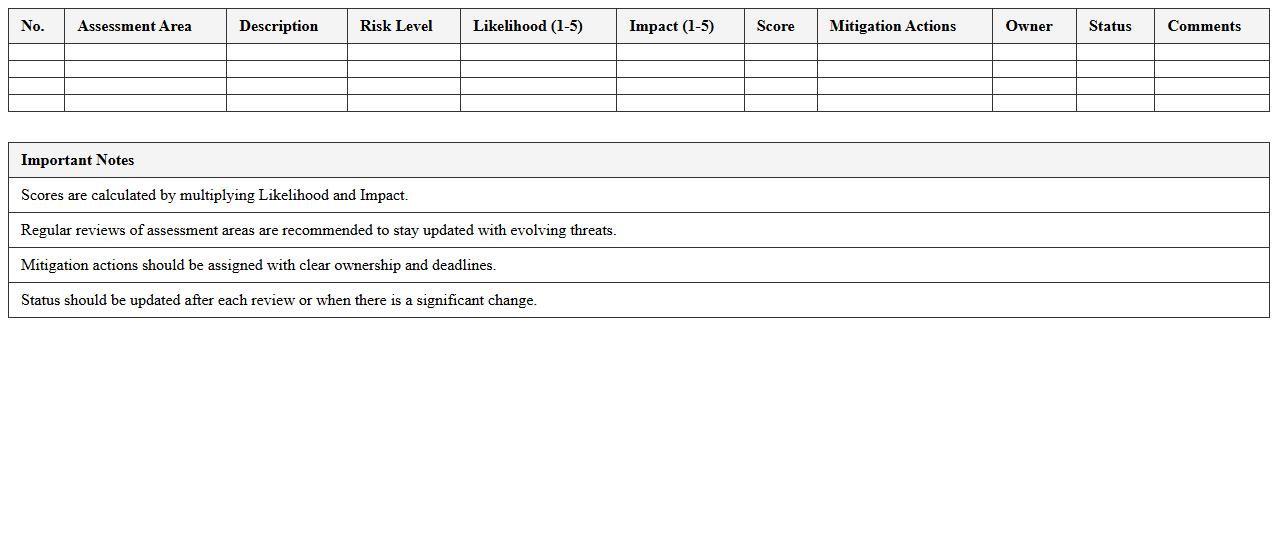
Vulnerability Assessment Scorecard Excel
The
Vulnerability Assessment Scorecard Excel document is a structured tool used to identify, evaluate, and prioritize security vulnerabilities within an organization's IT environment. It helps track weaknesses across systems and applications by assigning scores based on severity, likelihood, and potential impact, enabling focused risk management efforts. Utilizing this scorecard facilitates informed decision-making, targeted remediation, and improved overall security posture.
IT Risk Prioritization Spreadsheet
An
IT Risk Prioritization Spreadsheet is a tool designed to identify, evaluate, and rank potential IT risks based on their impact and likelihood. It helps organizations systematically manage cybersecurity threats, operational vulnerabilities, and compliance issues by providing a clear visual representation of risk levels. This document enables decision-makers to allocate resources effectively, ensuring critical risks are addressed promptly to minimize potential damage and optimize IT governance.
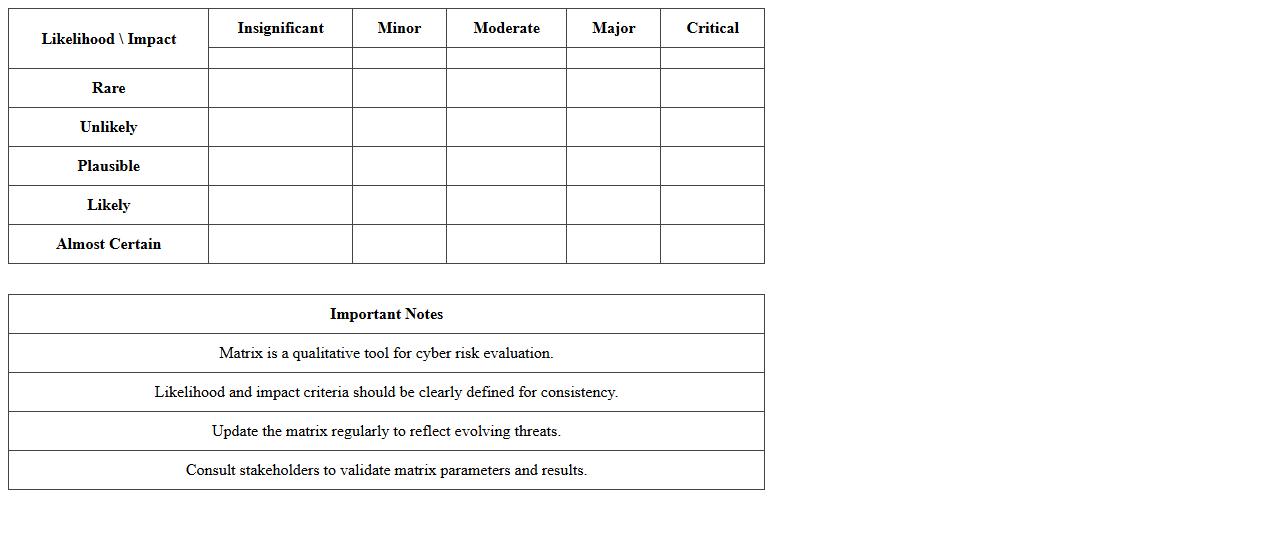
Cyber Risk Likelihood Impact Matrix Template
A
Cyber Risk Likelihood Impact Matrix Template document is a strategic tool used to assess and visualize the probability and potential impact of various cyber threats on an organization. It helps prioritize risks by categorizing them based on their likelihood of occurrence and the severity of their consequences, enabling targeted resource allocation for mitigation efforts. This template improves decision-making processes by providing a clear framework to identify critical vulnerabilities and focus cybersecurity initiatives effectively.
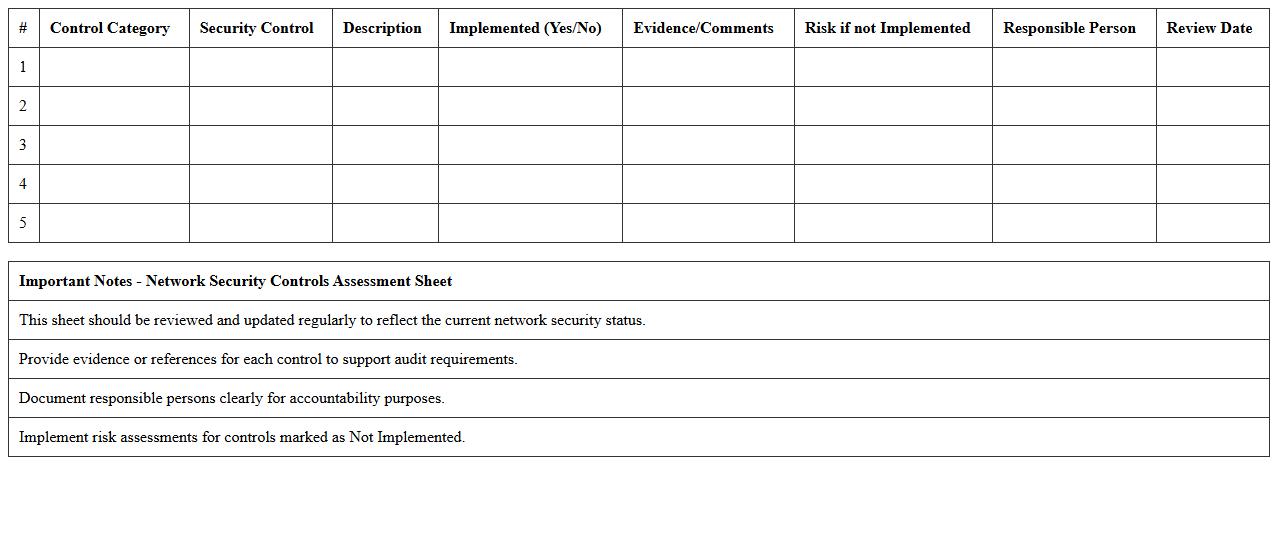
Network Security Controls Assessment Sheet
The
Network Security Controls Assessment Sheet is a comprehensive document designed to evaluate the effectiveness of implemented security measures within a network infrastructure. It systematically identifies vulnerabilities, monitors compliance with security policies, and ensures critical controls are in place to protect against unauthorized access, data breaches, and cyber threats. Utilizing this assessment sheet helps organizations maintain a robust security posture by enabling continuous improvement and informed decision-making based on detailed risk analysis and control effectiveness.
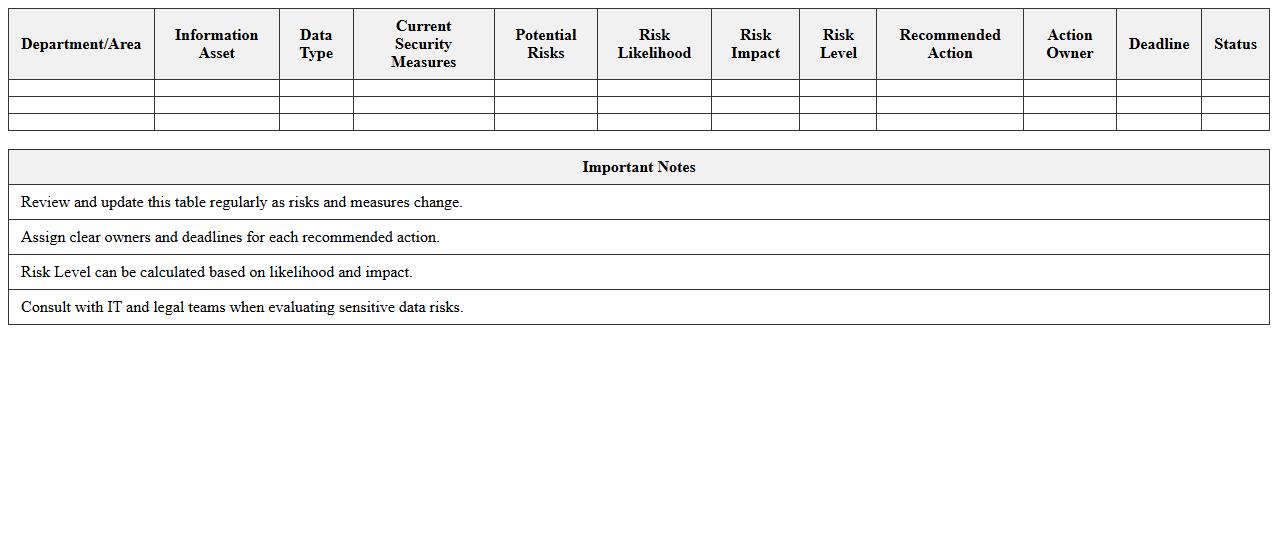
Data Breach Risk Evaluation Excel Template
The
Data Breach Risk Evaluation Excel Template document is a structured tool designed to assess and quantify the potential risks associated with data breaches within an organization. It helps identify vulnerabilities, estimate impact severity, and prioritize mitigation strategies by organizing data points such as threat likelihood, asset value, and security controls effectiveness. This template is useful for cybersecurity teams and risk managers to make informed, data-driven decisions that enhance overall data protection and compliance efforts.
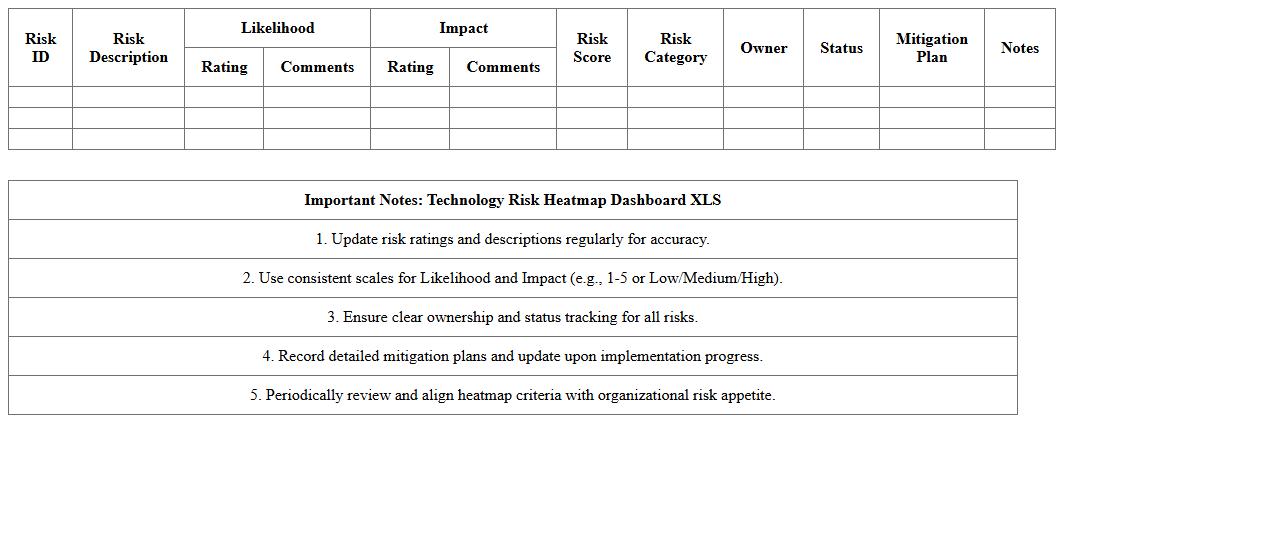
Technology Risk Heatmap Dashboard XLS
The
Technology Risk Heatmap Dashboard XLS document visually represents potential technology-related risks by categorizing them based on impact and likelihood, enabling organizations to prioritize risk management efforts effectively. It serves as a centralized tool for tracking, analyzing, and communicating risks, promoting proactive decision-making and resource allocation. This dashboard helps stakeholders quickly identify critical vulnerabilities and monitor risk mitigation progress in real-time.
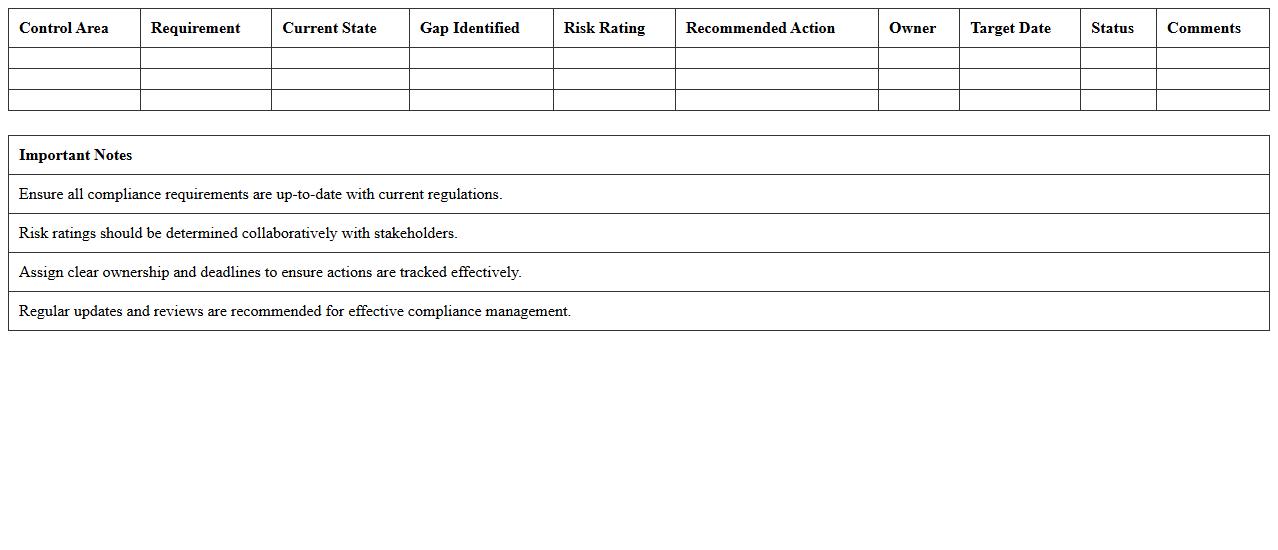
IT Compliance Gap Analysis Excel Template
The
IT Compliance Gap Analysis Excel Template document serves as a structured tool to identify discrepancies between current IT practices and regulatory or internal compliance requirements. It helps organizations systematically evaluate their adherence to standards such as GDPR, HIPAA, or ISO 27001 by highlighting areas that need improvement. Utilizing this template enables efficient risk mitigation, supports audit readiness, and ensures continuous alignment with compliance mandates.
How does the Excel template quantify IT risk severity for different cybersecurity threats?
The Excel template uses a quantitative scoring system to assess IT risk severity. It assigns numerical values based on factors like threat likelihood and potential impact. This method ensures a clear and consistent evaluation of various cybersecurity threats.
Are automated risk scoring formulas embedded in the document?
Yes, the document contains automated risk scoring formulas that calculate risk levels dynamically. These formulas integrate multiple risk factors to provide real-time updates. This automation enhances accuracy and efficiency in risk assessment.
Does the letter address compliance mapping (e.g., NIST, ISO) within the risk assessment?
The letter explicitly mentions compliance mapping aligned with standards like NIST and ISO. It explains how the risk assessment references these frameworks to ensure regulatory adherence. This approach supports comprehensive cybersecurity governance.
What controls validation checkpoints are included in the Excel document?
The Excel file includes controls validation checkpoints to verify the effectiveness of IT security measures. These checkpoints ensure that controls are properly implemented and functioning. Regular validations foster continuous risk management improvement.
Is stakeholder access and version control for the Excel file discussed in the letter?
The letter highlights stakeholder access protocols and version control practices for the Excel file. It emphasizes secure collaboration and tracks document changes over time. This ensures transparency and accountability during risk evaluations.