The Information Technology Risk Assessment Excel Template for Security Audits streamlines the evaluation of potential IT vulnerabilities and threats. It provides a structured format to identify, analyze, and prioritize risks, ensuring a comprehensive review of security controls. This template enhances audit efficiency by organizing data clearly for quick decision-making and mitigation planning.
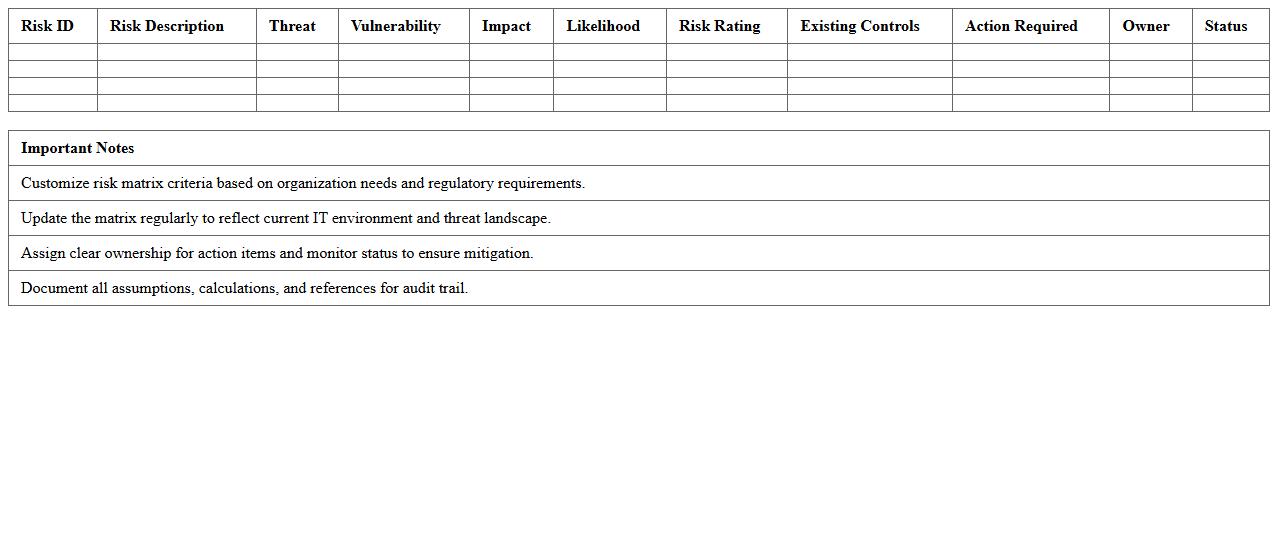
IT Risk Assessment Matrix for Security Audits - Excel Template
An
IT Risk Assessment Matrix for Security Audits - Excel Template is a structured tool designed to identify, evaluate, and prioritize potential security risks within an organization's IT infrastructure. This matrix helps quantify the likelihood and impact of various threats, enabling efficient resource allocation and informed decision-making to enhance cybersecurity measures. Businesses benefit from this template by streamlining the audit process, improving risk visibility, and ensuring compliance with security standards.
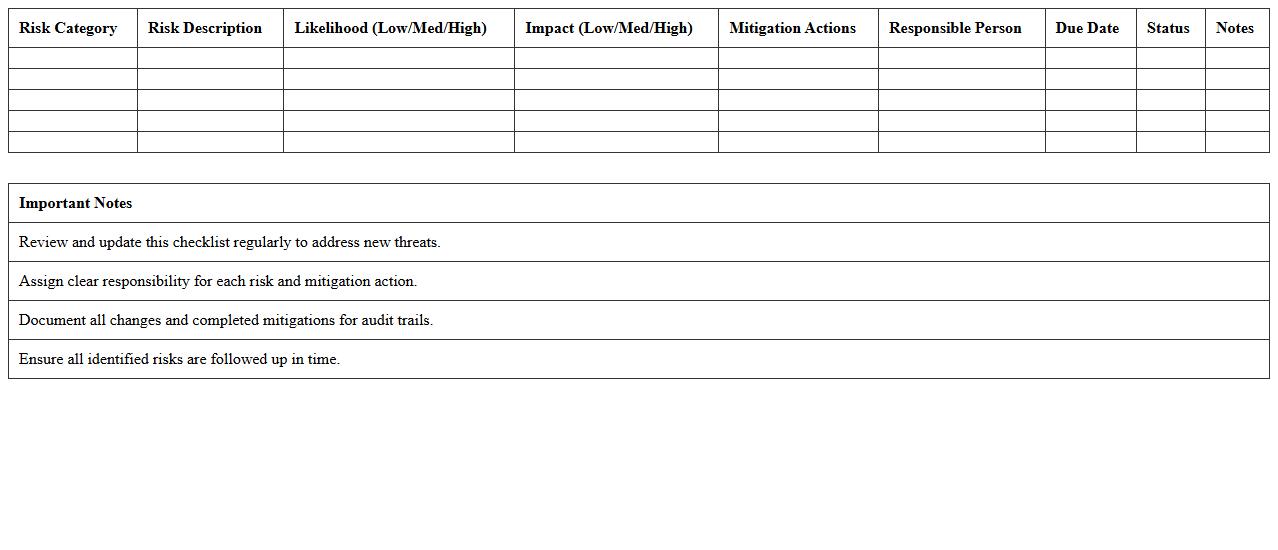
Cybersecurity Risk Evaluation Checklist - Excel Spreadsheet
The
Cybersecurity Risk Evaluation Checklist - Excel Spreadsheet is a structured tool designed to assess and document potential security vulnerabilities within an organization's information systems. This document allows users to systematically identify risks, prioritize mitigation efforts, and track progress in enhancing cybersecurity measures. Its spreadsheet format facilitates easy customization, data analysis, and reporting, making it an essential resource for improving security posture and compliance.
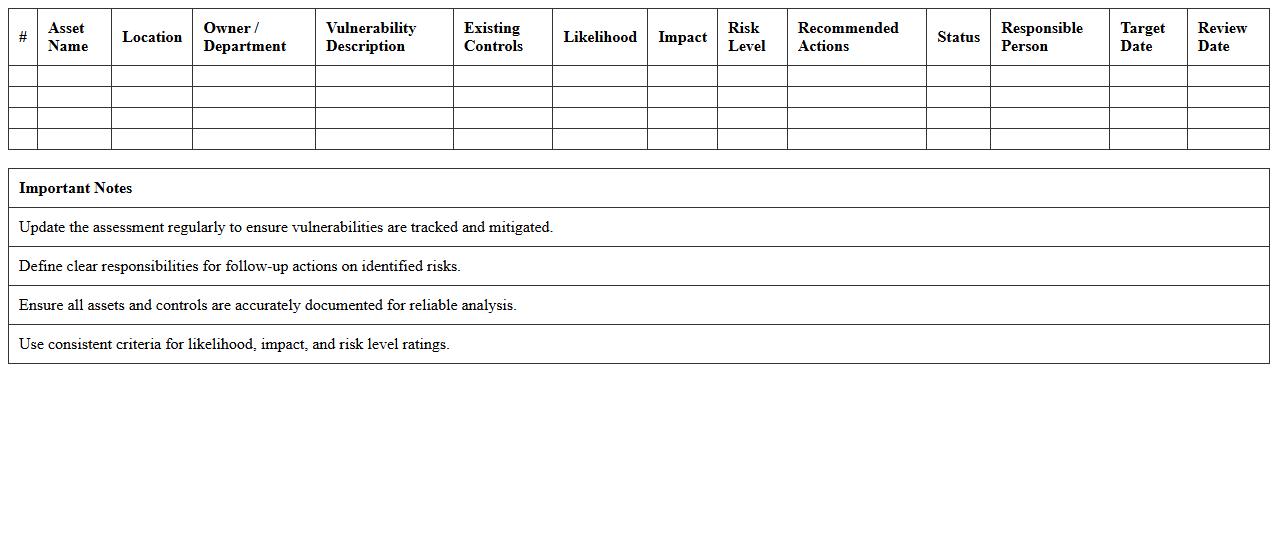
Information System Vulnerability Assessment - Excel Template
The
Information System Vulnerability Assessment - Excel Template is a structured tool designed to identify, analyze, and document potential security weaknesses within an organization's information systems. It allows users to systematically evaluate threats, prioritize risks, and track mitigation efforts, ensuring comprehensive visibility into system vulnerabilities. This template enhances risk management processes by providing clear, organized data that supports informed decision-making and strengthens overall cybersecurity posture.
IT Compliance and Risk Tracking Sheet - Excel Download
An
IT Compliance and Risk Tracking Sheet in Excel format is a structured document designed to monitor and evaluate IT-related compliance requirements and potential risks within an organization. This tool helps in systematically tracking regulatory standards, identifying vulnerabilities, and documenting mitigation measures, ensuring that IT operations align with legal and industry frameworks. Utilizing this sheet enhances risk management efficiency, supports audit preparedness, and promotes continuous compliance oversight across all IT processes.
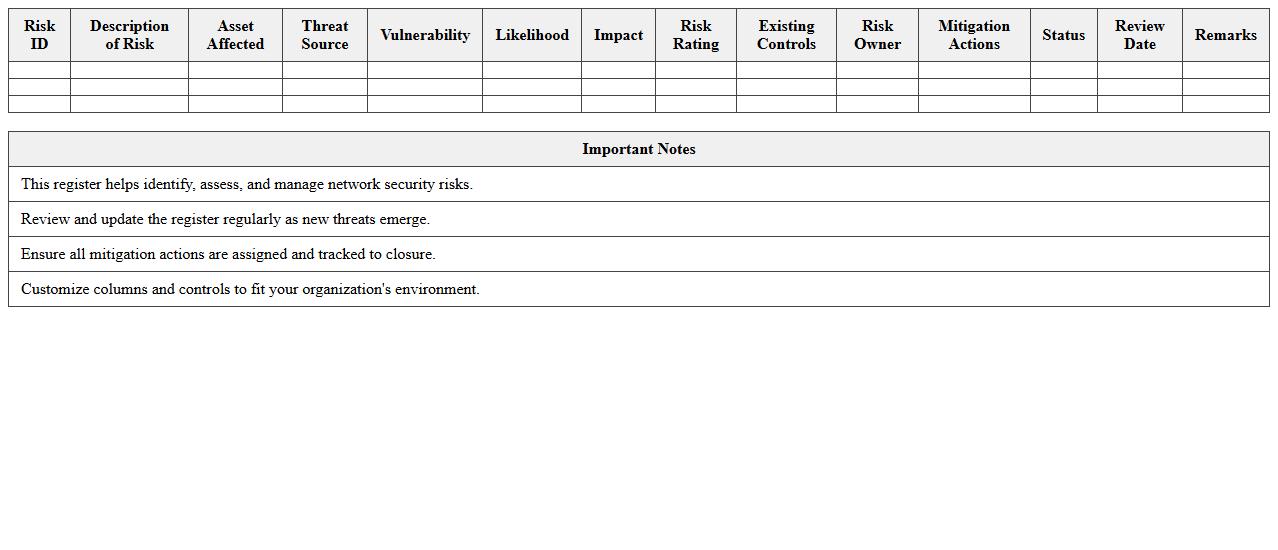
Network Security Risk Register - Excel Template
A
Network Security Risk Register - Excel Template document is a structured tool designed to identify, assess, and track potential security threats within a network infrastructure. It helps organizations systematically document vulnerabilities, evaluate their risk levels, and prioritize mitigation efforts to safeguard sensitive data. Utilizing this template enables efficient risk management, ensures compliance with security policies, and supports proactive decision-making to enhance overall network protection.
IT Audit Findings and Risk Log - Excel Tracker
An
IT Audit Findings and Risk Log - Excel Tracker document systematically records and monitors audit findings, identified risks, and their remediation status within an organization's IT environment. It helps streamline risk management by providing a centralized, structured overview of compliance issues, vulnerabilities, and mitigation actions. This tool improves accountability and facilitates timely decision-making by tracking progress and prioritizing IT risks effectively.
Data Security Risk Scoring Sheet - Excel Format
A
Data Security Risk Scoring Sheet - Excel Format is a structured document designed to evaluate and quantify potential security risks within an organization's data environment. It allows users to systematically assess vulnerabilities, assign risk scores based on severity and likelihood, and prioritize mitigation efforts effectively. This tool enhances decision-making by providing clear, data-driven insights into security gaps, facilitating proactive risk management and compliance with regulatory standards.
Application Security Gap Analysis - Excel Template
The
Application Security Gap Analysis - Excel Template is a structured document designed to identify vulnerabilities and security weaknesses within software applications. It helps organizations systematically compare current security measures against industry standards and best practices to reveal gaps. This tool is essential for prioritizing remediation efforts, improving cybersecurity posture, and ensuring compliance with regulatory requirements.
IT Threat Impact & Likelihood Assessment - Excel Sheet
The
IT Threat Impact & Likelihood Assessment Excel Sheet document systematically evaluates potential cyber threats by quantifying their impact and probability, enabling organizations to prioritize risks effectively. Its structured format helps IT teams identify vulnerabilities, allocate resources wisely, and develop targeted mitigation strategies. Utilizing this tool enhances overall cybersecurity posture by promoting data-driven decision-making and proactive risk management.
Information Security Risk Heat Map - Excel Template
The
Information Security Risk Heat Map - Excel Template document visually represents the likelihood and impact of security risks using a color-coded matrix, allowing organizations to prioritize threats effectively. This template simplifies risk assessment by clearly displaying vulnerabilities and their severity, enabling more informed decision-making for resource allocation and mitigation strategies. It is essential for maintaining robust cybersecurity, ensuring compliance, and minimizing potential data breaches or operational disruptions.
How does the Excel template ensure traceability of identified IT security risks to mitigation actions?
The Excel template ensures traceability by linking each identified IT security risk to specific mitigation actions within the spreadsheet. It uses unique identifiers and cross-referencing columns to maintain clear connections between risks and responses. This structured approach allows for easy tracking and review of risk management efforts.
Are automated macros used in the assessment sheet to highlight non-compliant controls?
The assessment sheet employs automated macros to efficiently identify and highlight non-compliant controls. These macros scan the data for discrepancies and flag issues using conditional formatting tools. This automation significantly enhances the accuracy and speed of compliance reviews.
Does the document include fields for mapping risks to specific compliance frameworks (e.g., ISO 27001, NIST)?
The document incorporates dedicated fields to map risks directly to recognized compliance frameworks such as ISO 27001 and NIST. This feature helps align the risk management process with industry standards and regulatory requirements. It ensures that controls and risks are properly categorized under relevant compliance criteria.
Can the Excel file generate risk heat maps or visual dashboards for audit presentations?
The Excel file is designed to generate dynamic risk heat maps and visual dashboards, facilitating impactful audit presentations. It uses built-in charting tools and conditional formatting to represent risk severity and likelihood visually. These graphical displays aid stakeholders in understanding and prioritizing IT security risks.
How does the letter document roles and responsibilities for updating and maintaining the risk register?
The letter clearly outlines specific roles and responsibilities for team members managing the risk register. It designates accountable individuals for regular updates, reviews, and maintenance activities. This clarity ensures consistent oversight and governance of the risk management process.
More Information Technology Excel Templates