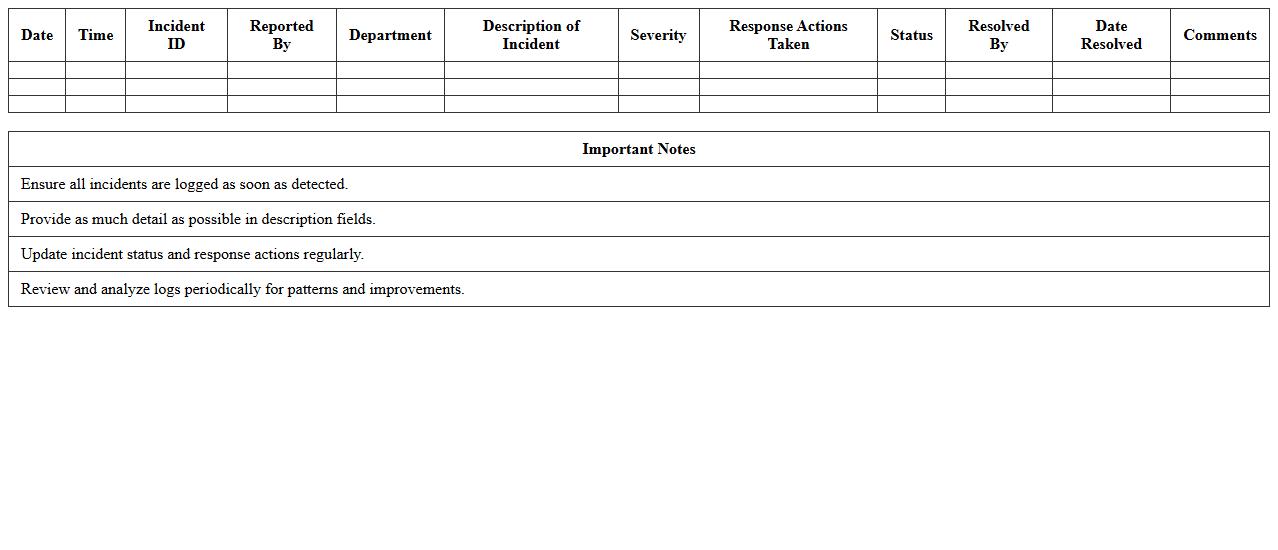
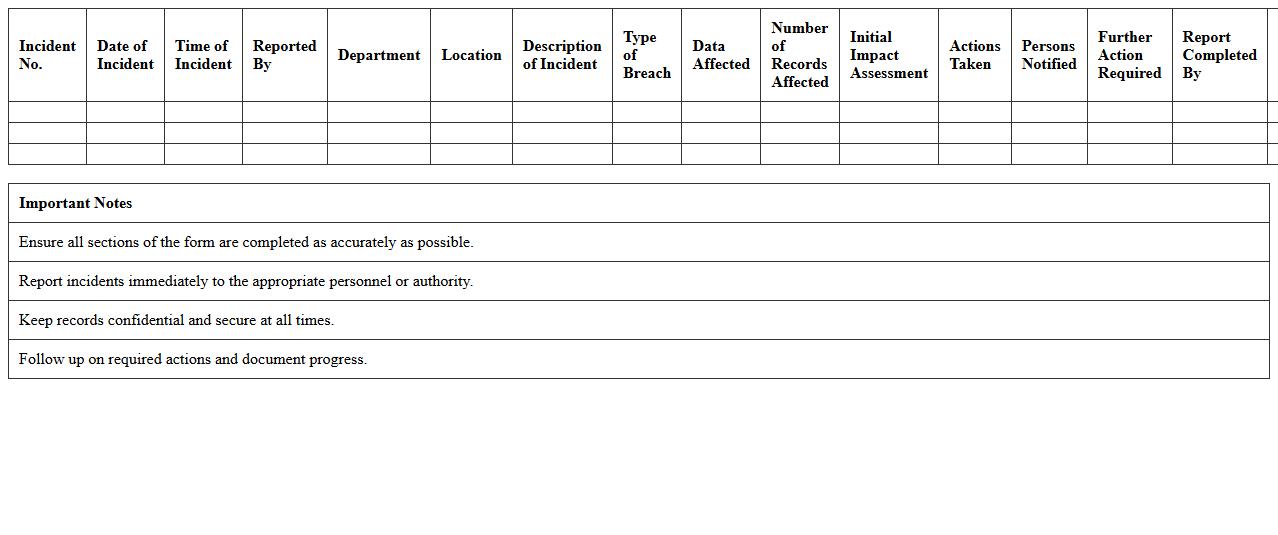
IT Security Incident Log Spreadsheet Template
An
IT Security Incident Log Spreadsheet Template is a structured document designed to record and track cybersecurity incidents systematically. It helps organizations document details such as incident type, date, severity, response actions, and resolution status, enabling efficient monitoring and auditing. This template improves incident management by providing clear visibility into threats, supporting compliance efforts, and enhancing decision-making for future security measures.
Cybersecurity Incident Report Tracker Excel
A
Cybersecurity Incident Report Tracker Excel document is a structured tool designed to log, monitor, and analyze cybersecurity incidents in real-time. This tracker enables organizations to efficiently document threat details, incident status, response actions, and resolution timelines, facilitating quick identification and mitigation of vulnerabilities. By centralizing incident data, it enhances accountability, supports compliance reporting, and helps improve overall security posture through informed decision-making.
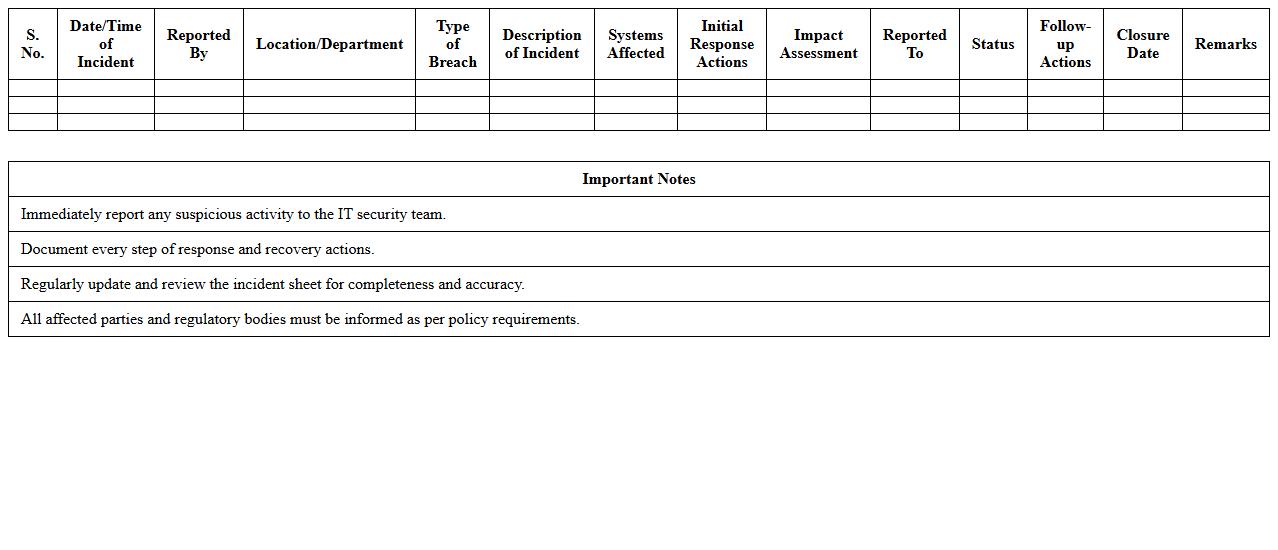
Network Security Breach Incident Excel Sheet
A
Network Security Breach Incident Excel Sheet document is a structured tool designed to record and analyze details of cybersecurity breaches, including time, affected systems, breach type, and response actions. It enables organizations to monitor vulnerabilities, track incident trends, and evaluate the effectiveness of security protocols over time. Utilizing this document enhances incident management efficiency and supports data-driven decisions to strengthen overall network protection.
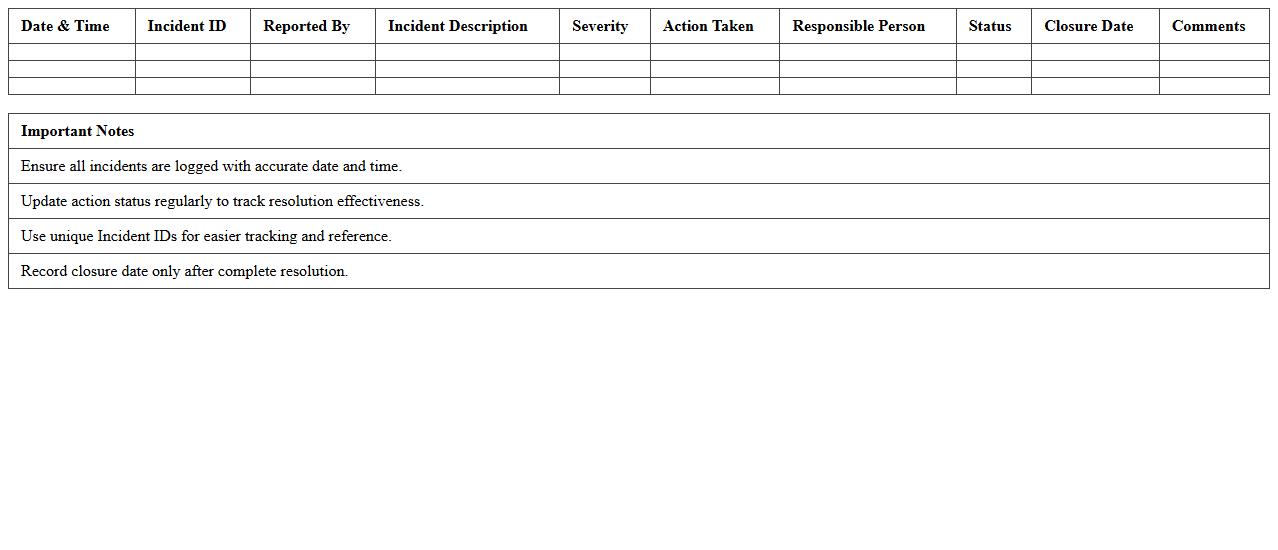
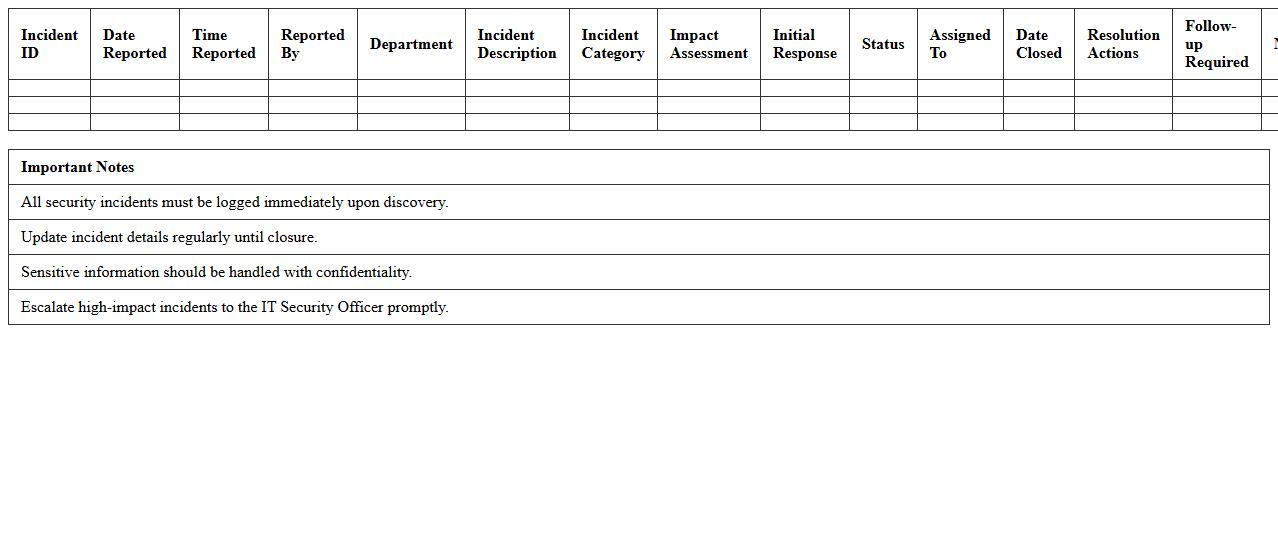
IT Incident Response Action Log Template
An
IT Incident Response Action Log Template is a structured document designed to systematically record all actions taken during an IT incident, including timestamps, responsible personnel, and incident details. This template enhances clarity and accountability by providing a chronological overview of incident responses, crucial for identifying resolution timelines and decision-making effectiveness. Utilizing this log ensures efficient communication among IT teams, supports post-incident analysis, and helps improve future incident management strategies.
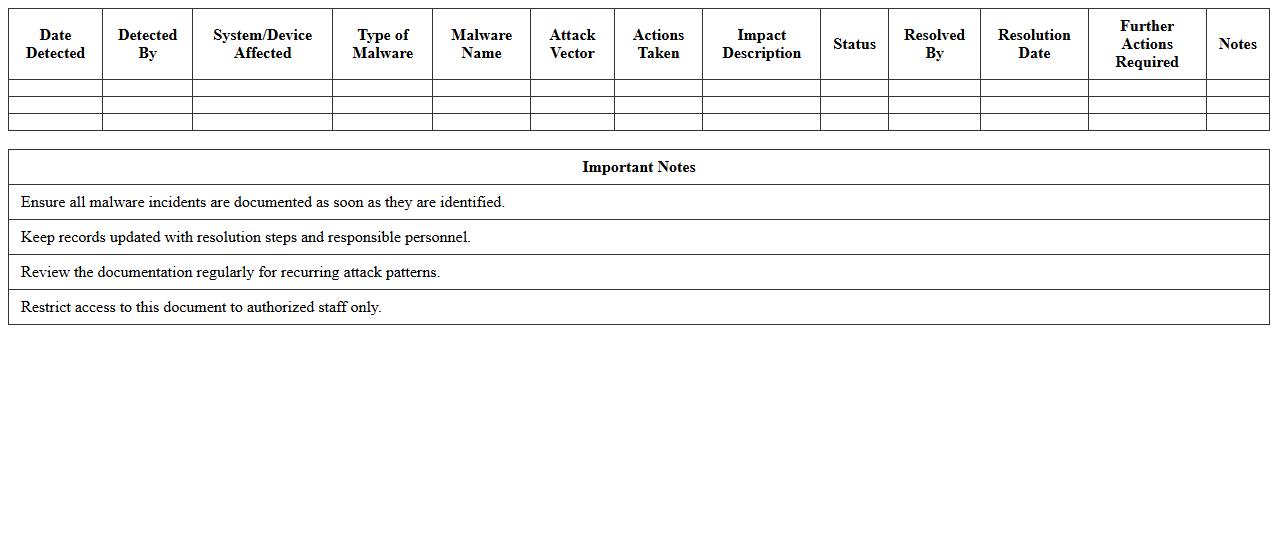
Malware Attack Documentation Excel Template
The
Malware Attack Documentation Excel Template is a structured spreadsheet designed to record and analyze details of malware incidents systematically. It helps cybersecurity teams track attack vectors, malware type, affected systems, and response measures, enhancing incident management efficiency. Using this template enables organizations to identify patterns and improve future threat mitigation strategies.
Data Breach Incident Report Form Excel
The
Data Breach Incident Report Form Excel document is a structured template designed to capture critical information related to data breach events, including the nature, scope, and impact of the breach. This form enables organizations to systematically document incidents, ensuring comprehensive data collection for compliance, risk analysis, and remedial action planning. Utilizing this report form enhances incident response efficiency and supports regulatory reporting requirements by maintaining accurate, organized breach records.
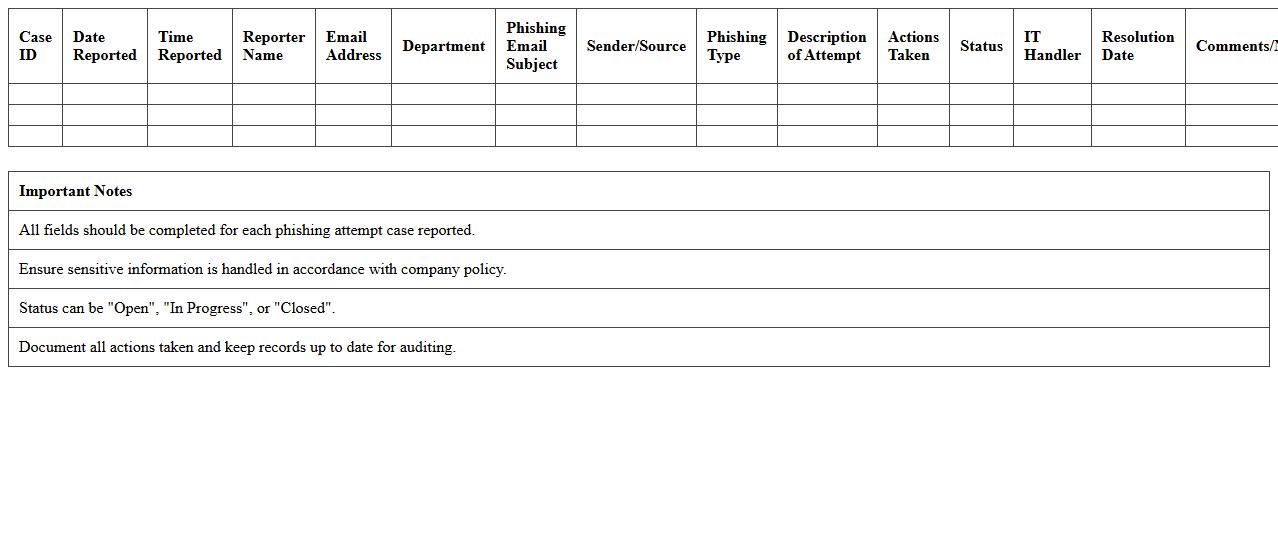
Phishing Attempt Case Report Excel Sheet
The
Phishing Attempt Case Report Excel Sheet document is a structured tool designed to log and analyze phishing incidents, capturing details such as attack vectors, targeted users, and response actions. It facilitates efficient tracking of phishing trends, enabling organizations to identify vulnerabilities and enhance cybersecurity measures. Using this report helps in systematically documenting cases, improving incident response times, and supporting compliance with security policies.
Security Event Timeline Tracker Excel Template
The
Security Event Timeline Tracker Excel Template is a structured document designed to log and monitor security incidents over time, providing a clear visual timeline of events such as breaches, alerts, and responses. It helps security teams analyze patterns, identify recurring threats, and improve incident response strategies by consolidating data in an organized, easily accessible format. This template enhances risk management by enabling faster decision-making and ensuring compliance with security protocols.
IT Helpdesk Security Incident Register
The
IT Helpdesk Security Incident Register document is a centralized record that tracks all reported security incidents, including details such as incident type, date, affected systems, and resolution status. It is useful for identifying recurring vulnerabilities, ensuring timely incident response, and facilitating compliance with cybersecurity policies and regulatory requirements. Maintaining this register enhances organizational transparency and supports continuous improvement in IT security management.
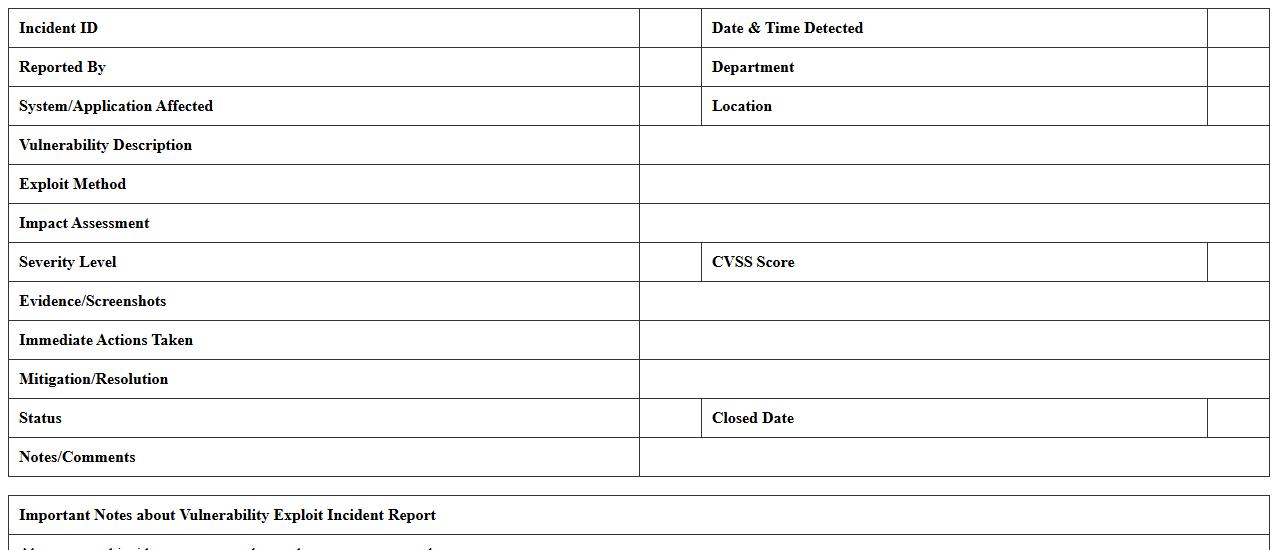
Vulnerability Exploit Incident Report Excel
A
Vulnerability Exploit Incident Report Excel document is a structured spreadsheet used to log, track, and analyze security breaches caused by exploiting software or system vulnerabilities. It helps cybersecurity teams systematically document the nature, impact, and resolution status of each incident, enabling efficient prioritization and mitigation. This tool supports data-driven decision-making by providing clear visibility into recurring threats and effectiveness of security measures.
What are the key data fields to include in an IT incident report Excel template for security events?
When creating an IT incident report Excel template, it's crucial to include fields such as Incident ID, Date and Time, and Incident Type for clear identification. Additionally, fields like Description, Affected Systems, and Severity Level help provide detailed context and impact assessment. Including Status, Assigned To, and Resolution Time completes the dataset for tracking incident progress and accountability.
How can automated Excel formulas assist in incident severity classification?
Automated Excel formulas can classify incident severity by analyzing parameters like impact and urgency using nested IF statements or VLOOKUP functions. Formulas can dynamically update severity based on predefined thresholds, reducing manual errors and speeding decision-making. This automation ensures consistent classification aligned with security protocols.
Which Excel chart types best visualize incident frequency trends for security teams?
Line charts and bar charts are the most effective for visualizing incident frequency trends over time, allowing security teams to identify patterns and spikes. Pivot charts can further enhance analysis by segmenting incidents by category or severity. These visual tools aid in proactive monitoring and reporting.
What conditional formatting rules help highlight unresolved security incidents in Excel?
Applying conditional formatting rules such as color scales or icon sets to the Status field can instantly highlight unresolved or pending security incidents. For example, red fill colors or warning icons for "Open" or "In Progress" statuses draw attention quickly. This visual differentiation enhances incident management efficiency.
How can macros in Excel streamline the documentation of recurring security incident types?
Excel macros automate repetitive tasks by capturing incident details and populating standardized templates for recurring event types, saving valuable time. Macros can also generate summary reports or update logs with a single click, increasing consistency and reducing human error. This streamlines documentation and supports faster incident response.