Information Technology Security Incident Tracking Excel Template
The
Information Technology Security Incident Tracking Excel Template document is designed to efficiently record, monitor, and analyze security incidents within an organization. It enables IT professionals to systematically track incidents such as data breaches, malware attacks, and unauthorized access, ensuring timely response and mitigation. This template enhances incident reporting accuracy, supports compliance with security policies, and provides valuable insights for improving overall cybersecurity posture.
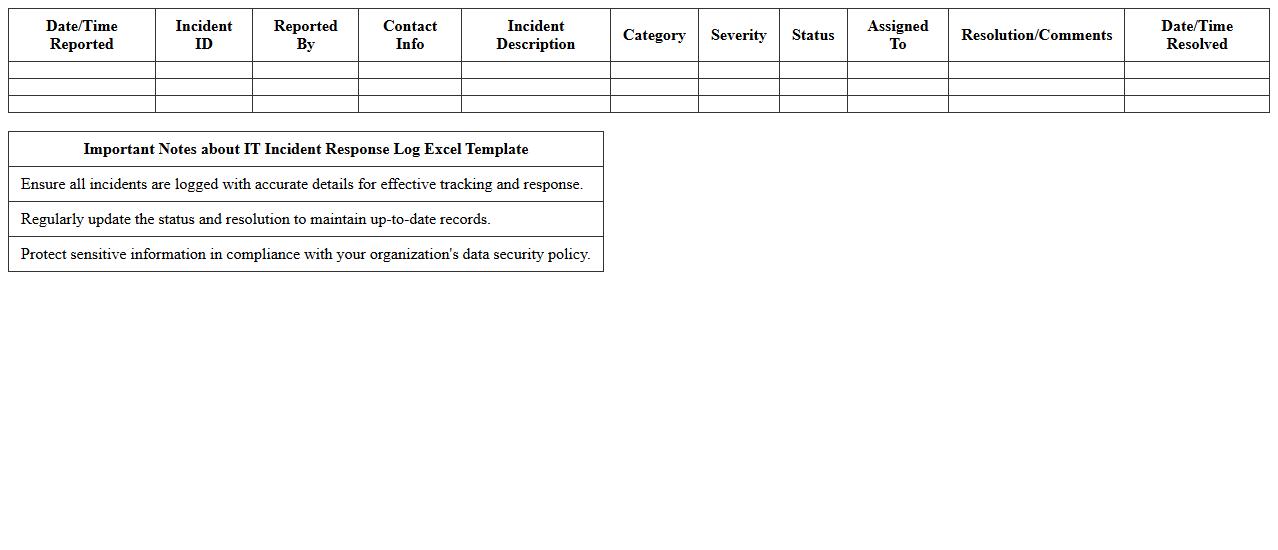
IT Incident Response Log Excel Template
An
IT Incident Response Log Excel Template document is a structured tool designed to systematically record and track IT incidents, including details such as incident type, time of occurrence, response actions, and resolution status. It facilitates efficient incident management by enabling quick access to historical data, helping IT teams identify patterns, improve response times, and maintain compliance with organizational policies. This template enhances communication among stakeholders and supports continuous improvement in IT service reliability.
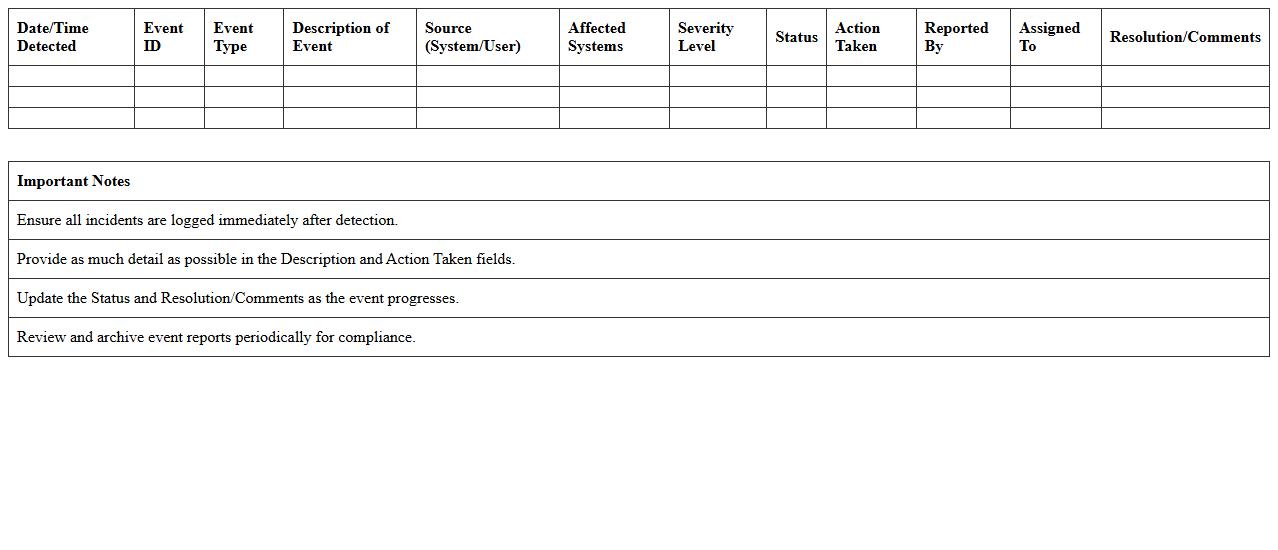
Cybersecurity Event Report Excel Spreadsheet
A
Cybersecurity Event Report Excel Spreadsheet document is a structured tool that records and organizes data related to cybersecurity incidents, including types of threats, affected systems, and response actions. It facilitates the analysis of event trends, detection of vulnerabilities, and tracking of mitigation efforts, enabling teams to strengthen their security posture. This spreadsheet enhances incident management by providing a clear, accessible overview of cybersecurity activities for timely decision-making and compliance reporting.
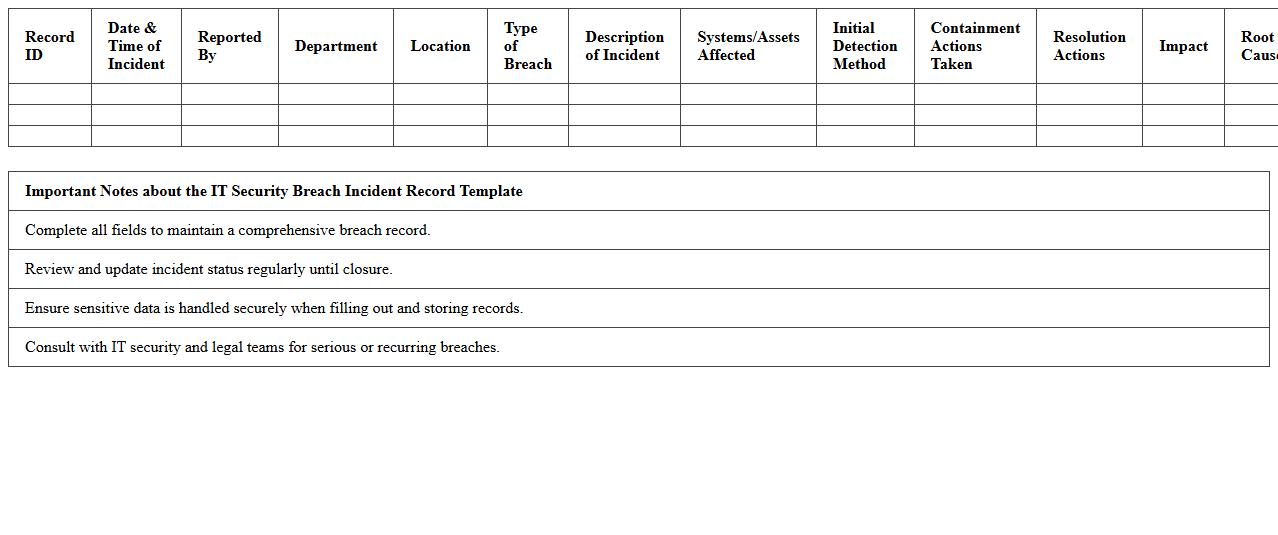
IT Security Breach Incident Record Template
The
IT Security Breach Incident Record Template document is a structured form designed to capture detailed information about security breaches, including the nature, scope, and impact of the incident. It enables organizations to systematically document and analyze breaches for compliance, investigation, and remediation purposes. By maintaining accurate records, companies can improve cybersecurity measures, enhance incident response, and meet regulatory requirements effectively.
Technology Security Incident Summary Excel Sheet
The
Technology Security Incident Summary Excel Sheet document serves as a centralized tool to record, track, and analyze security incidents within an organization's IT infrastructure. It provides detailed insights into incident types, timelines, affected systems, and response actions, enabling proactive risk management and compliance reporting. Utilizing this sheet enhances the ability to quickly identify patterns, improve security protocols, and support incident resolution efforts effectively.
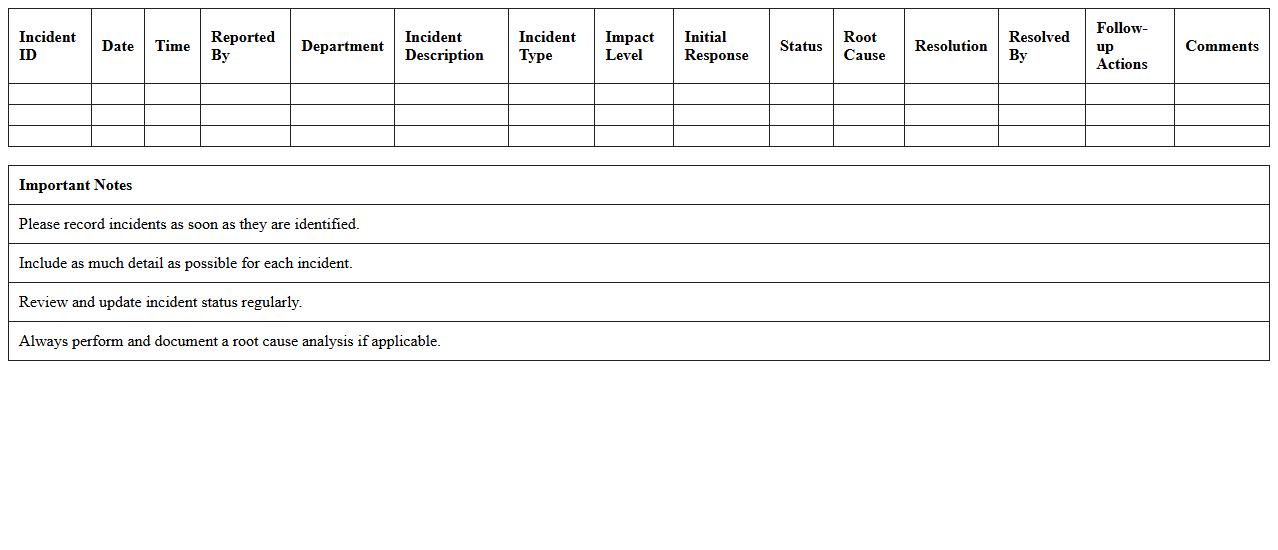
IT System Issue and Incident Register Template
An
IT System Issue and Incident Register Template document is a structured tool used to log, track, and manage IT-related problems and incidents systematically. This template helps organizations maintain a comprehensive record of issues, monitor their status, identify recurring problems, and facilitate timely resolution. By using this register, IT teams improve accountability, enhance communication, and ensure efficient incident management to minimize downtime and impact on business operations.
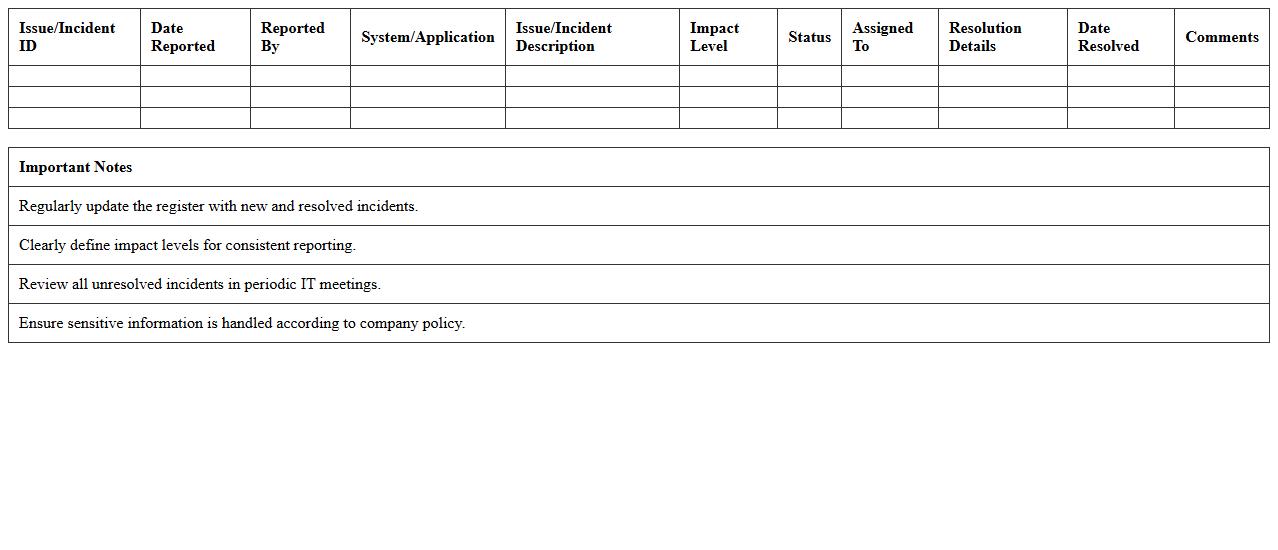
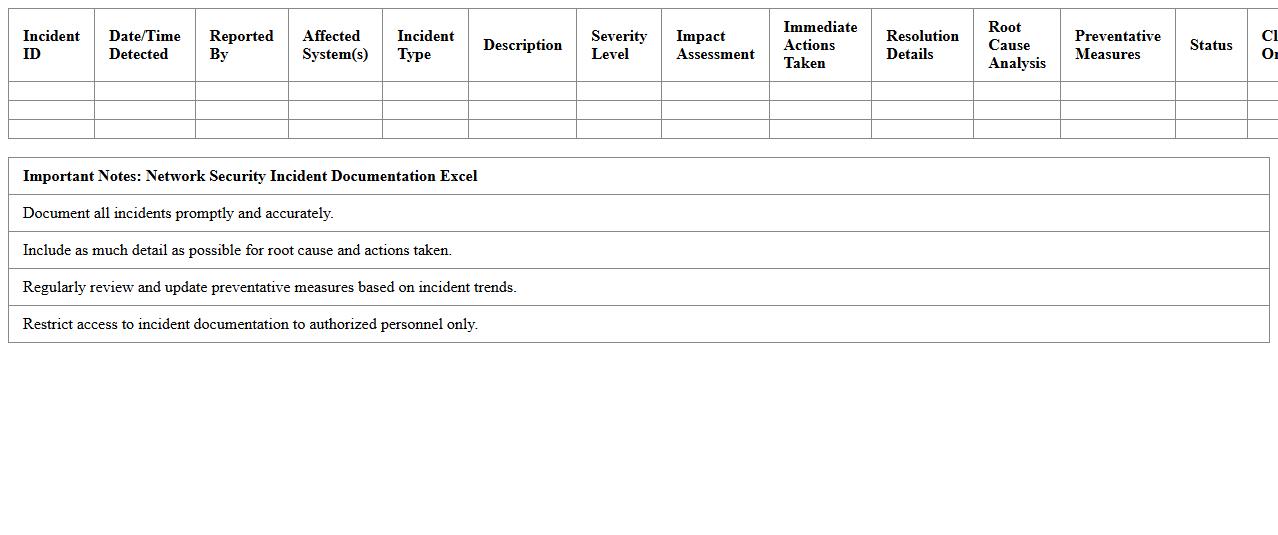
Network Security Incident Documentation Excel
The
Network Security Incident Documentation Excel document serves as a structured log for recording details of security breaches, cyber threats, and anomalies within a network environment. It enables organizations to systematically track incidents, analyze patterns, and respond promptly to mitigate risks. This documentation is essential for compliance auditing, post-incident reviews, and enhancing overall cybersecurity strategies by providing clear, organized data for decision-makers.
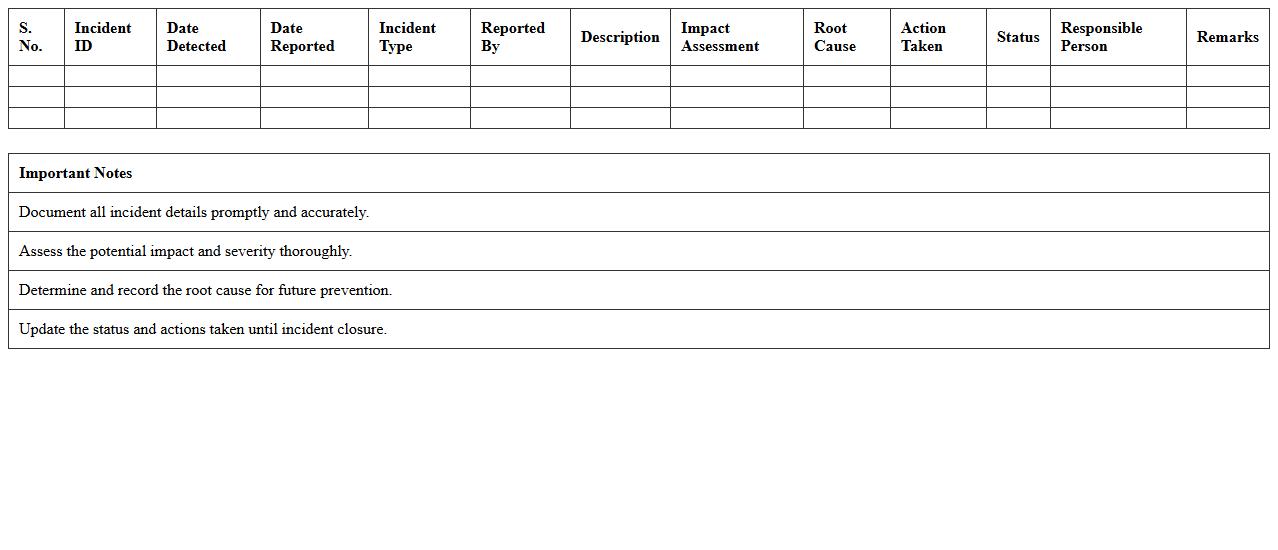
Information Security Incident Analysis Sheet
The
Information Security Incident Analysis Sheet document serves as a critical tool for systematically recording and analyzing the details of security incidents, including the nature, impact, and response actions taken. This structured approach helps organizations identify vulnerabilities, track incident patterns, and improve their overall cybersecurity posture by enabling informed decision-making and timely mitigation efforts. Using this document supports compliance with industry standards and enhances the ability to prevent future incidents through thorough root cause analysis.
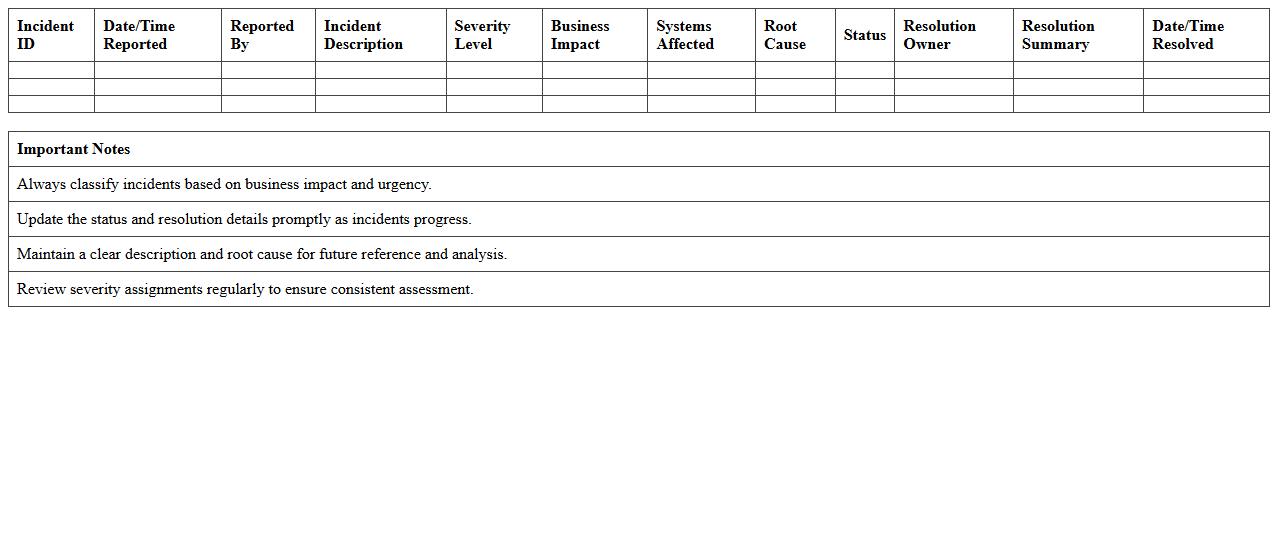
IT Incident Severity Assessment Excel Template
The
IT Incident Severity Assessment Excel Template is a structured tool designed to evaluate and categorize IT incidents based on their impact and urgency. This template helps IT teams quickly determine the priority level of an incident, enabling faster response times and efficient resource allocation. By systematically documenting incidents, organizations improve incident management workflows and minimize downtime.
Security Incident Remediation Tracker Spreadsheet
A
Security Incident Remediation Tracker Spreadsheet document is a detailed tool designed to log, monitor, and manage the resolution process of security incidents within an organization. It provides a structured format to track incident details, assigned responsibilities, remediation steps, deadlines, and status updates, ensuring timely and efficient mitigation of security risks. Using this spreadsheet enhances accountability, improves communication among security teams, and supports compliance with regulatory requirements by maintaining a clear record of how incidents are addressed.
What key fields should be included in an IT incident report Excel template for rapid threat assessment?
An effective IT incident report Excel template must include Incident ID, Date and Time, and Reporter details for precise tracking. It should also have fields for Incident Type, Description, and Impact Assessment to facilitate rapid threat assessment. Including Response Priority and Status helps teams quickly identify and act on critical security issues.
How can Excel automate severity scoring in security incident documentation?
Excel can automate severity scoring by using conditional formulas that evaluate incident criteria such as impact and urgency levels. Utilizing functions like IF(), VLOOKUP(), and nested formulas enables dynamic calculation of a severity score based on predefined rules. This automation streamlines prioritization by instantly updating severity as incident details change.
What formulas help timestamp and track incident response actions within the spreadsheet?
The NOW() and TODAY() functions automatically generate timestamps for logging incident detection and response actions. Tracking response duration can be managed with formulas like =END_TIME - START_TIME, calculating elapsed time between status updates. Combined with data validation lists, these formulas ensure consistent and accurate incident response documentation.
How do you structure an Excel sheet to link incident records with evidence attachments securely?
Structuring the sheet with a dedicated Attachment URL or Path column allows linking each incident to its evidence files stored on a secure server. Using Data Validation restricts entry to valid paths, ensuring evidence is properly referenced. Protecting the sheet with Password Encryption restricts unauthorized access to sensitive attachment information.
What methods support multi-user collaboration on an IT incident Excel document without data loss?
Utilizing Excel Online or OneDrive enables real-time multi-user collaboration with automatic version control. Implementing track changes and conflict resolution features prevents data loss during simultaneous edits. Additionally, enabling shared workbook options and regular backups maintains data integrity across user sessions.